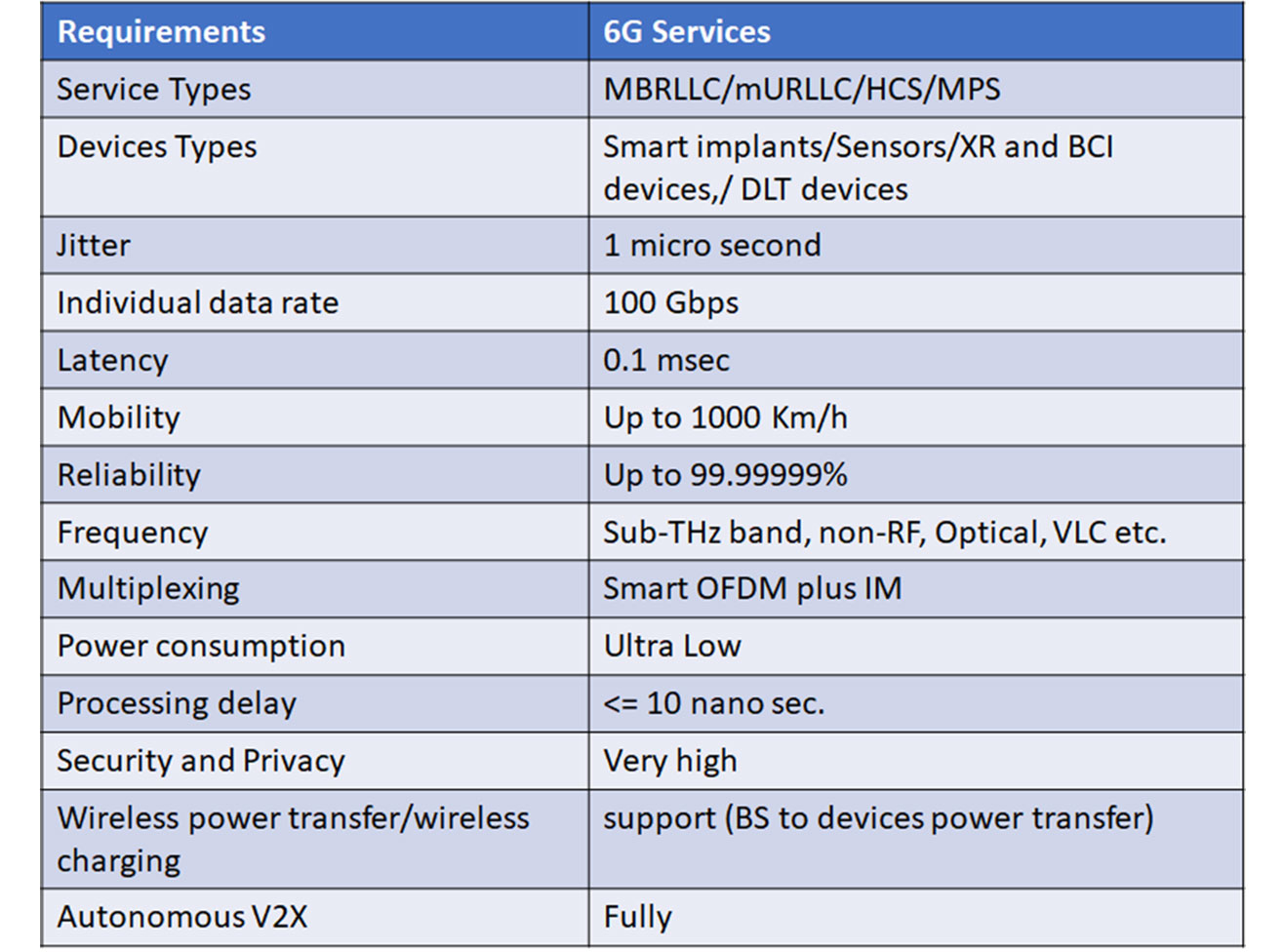
As 5G communication networks are being deployed for industrial and commercial applications, 6G communication also has drawn the attention of the end users. This is due to the increase in data-centric intelligent applications, which also challenged the capacity and features of 5G. For example, the existing delay in internet-based telemedicine applications is about 1msec, whereas the requirement is less than 0.1msec., which is not satisfied by the ultra-high bandwidth and low-latency features of 5G communication. This limitation of 5G cannot gratify the high communication and low latency requirements of data-centric industrial and healthcare services. As a result, Universities and Industries have started developing 6G technology with the requirements of higher bandwidth and reliability, better QoS and coverage, low-latency and power consumption, better privacy, and security. The key performance indicators of 6G communication are specified in Table(1). 6G is a revolutionary generation of wireless communication with the added dimensions of intelligence and autonomy to bring new vigor and vitality into next-generation communication because it can sense the situation and adoptively fix the bandwidth.
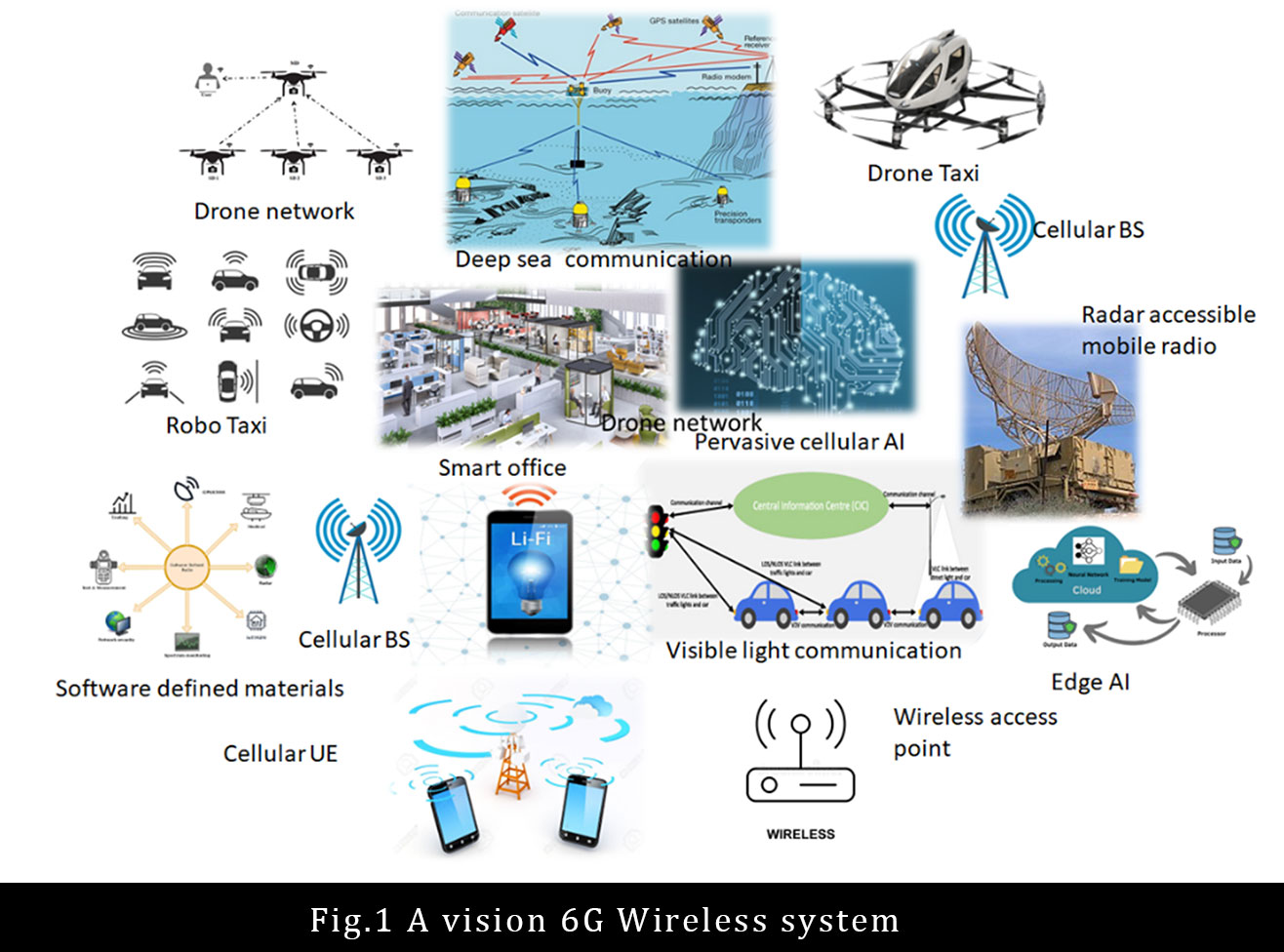
The use of AI along with other intelligent technologies enables a paradigm shift to transform the 5G features into an intelligent network. 6G communication is also augmented with various other new technologies to enhance spectral efficiency. This includes the technologies such as index modulation (IM), intelligent reflecting surface (IRS), visible light communication (VLC), sub-Terahertz (sub-THz), and Terahertz (THz) with a frequency range of 100GHz to 3THz. 6G communication proliferates the integration of space-air-ground-sea networks (SAGSIN), to establish the link between all networking nodes in the environment from the sky to the deep-sea. The use of blockchain to efficiently manage the spectrum resources will eliminate the challenges of spectral allocation from a centralized database.
Table1: Specification of 6G
To protect the data and minimize security attacks, 6G adopts edge-computing technologies, to support emerging applications such as metaverse, smart healthcare, holography radio, and support the networking services such as smart wearables devices, autonomous devices, 3D mapping, blockchain, etc.
Security challenges in 6G and Quantum Communication:
Many technologies explained above are proven for providing better security services in 6G communication. 6G presents different types of new security challenges due to the ultra-dense heterogeneous networks and many different types of connected devices. The new technology must ensure security over multiple trust domains.
Quantum computing has several applications in 6G communication. Security and reliability are the two major interests of quantum computing. In quantum communication, if an attacker changes something the quantum status will be changed. Quantum communication assisted 6G communication is for replacing the traditional communication channel to achieve extremely high reliability. Classical cryptography with traditional encryption and authentication may not be suitable for 6G. To provide better security the public-private key cryptosystem can be created by using quantum computing methods.
Quantum computers currently cannot solve the existing cryptographic problems with the available number of qubits. Solve these problems, it needs millions of qubits. Only with quantum cryptographic algorithms, we can fix this problem. Combining post-quantum computing security scenarios with the security mechanisms applicable may ensure privacy and security in the 6G communication channel with machine learning technique. Many 6G applications uses quantum security mechanism with quantum key distribution (QKD). For the ease of implementation quantum cryptography in 6G, NIST has proposed numerous new standards. This enables 6G to deliver secure data communication including QKD, quantum cryptography-enabled communication, and key sharing features such as quantum teleportation, super dense coding, and entanglement distribution.
Dr. Rathnakar Achary
Associate professor
Alliance College of Engineering and Design
